How to calculate signature?
1. Description#
API Gateway verifies the identity of each API request, and the server will also verify whether the call parameters are valid. Therefore, each HTTP request must contain the signature information. The requests with invalid signature will be rejected.
API Gateway verifies the identity of the requests by the token that are assigned to your application. The token is used to generate the signature string in the HTTP request URL and server-side signature string. It must be kept strictly confidential.
If you compose HTTP request manually (instead of using the official SDK), you need to understand the following signature algorithm.
The process of generating the signature is as follows:
- Sort all request parameters (including system and application parameters, but except the “signature” and parameters with byte array type) according to the parameter name in ASCII table. For example:
- concat all the key:value pairs into a string like '=' ':' ',' (Only outside the variable. Other values like "chanel":"alipay,wechat" keep "alipay,wechat". ) Concatenate the sorted parameters and their values into a string. For example:
- Add API path in front of the concatenated string. For example, adding the API name “/test/api”:
- Encode the concatenated string in UTF-8 format and make a digest by the signature algorithm (using HMAC_SHA256). For example:
- Convert the digest to hexadecimal format. For example:
2. Samples#
Please find below some samples on how to caculate signature based on token(secret), API, and parameters.
2.1. PYTHON#
2.2. JAVA#
2.3. C##
For the signature sample codes in other programming languages, refer to the source code of the official SDK.
3. Where can I find the token?#
You can find the token(secret) for generating the signature by login to the API gateway.
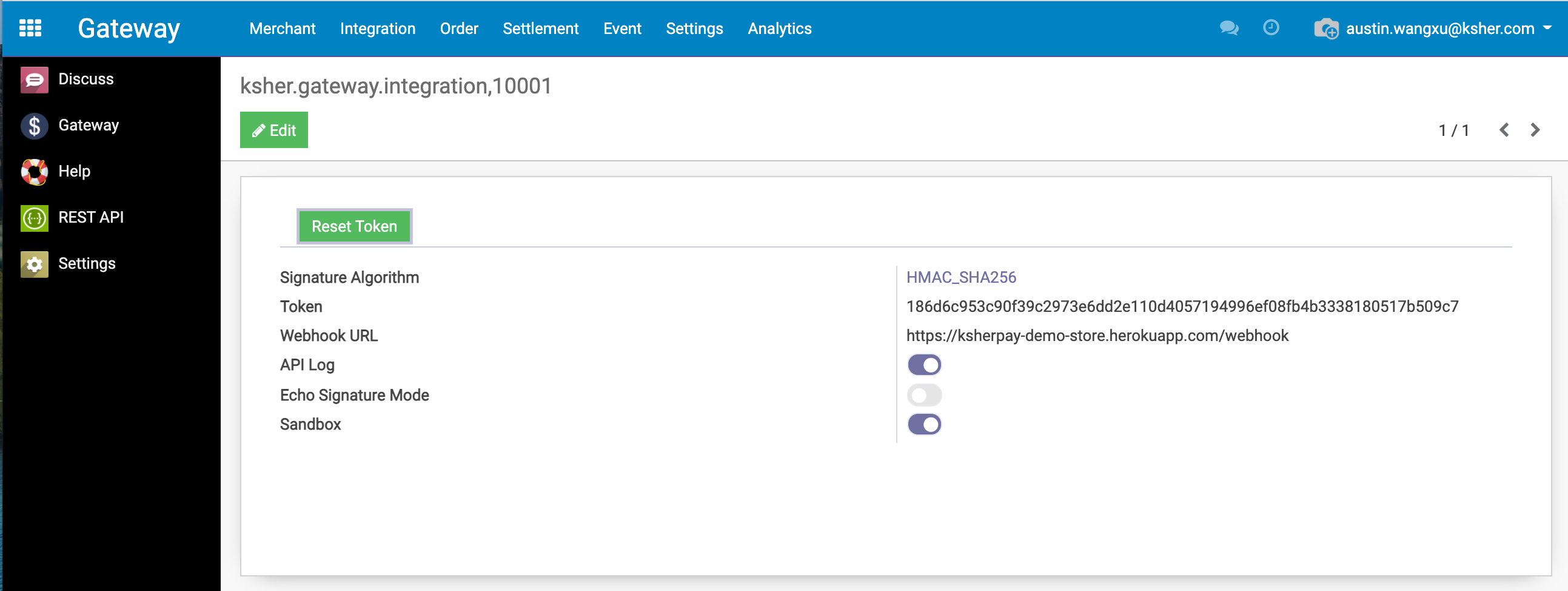
In the example above 186d6c953c90f39c2973e6dd2e110d4057194996ef08fb4b3338180517b509c7 is the token.
4. How to debug signature error?#
There are two debugging features in the sandbox.
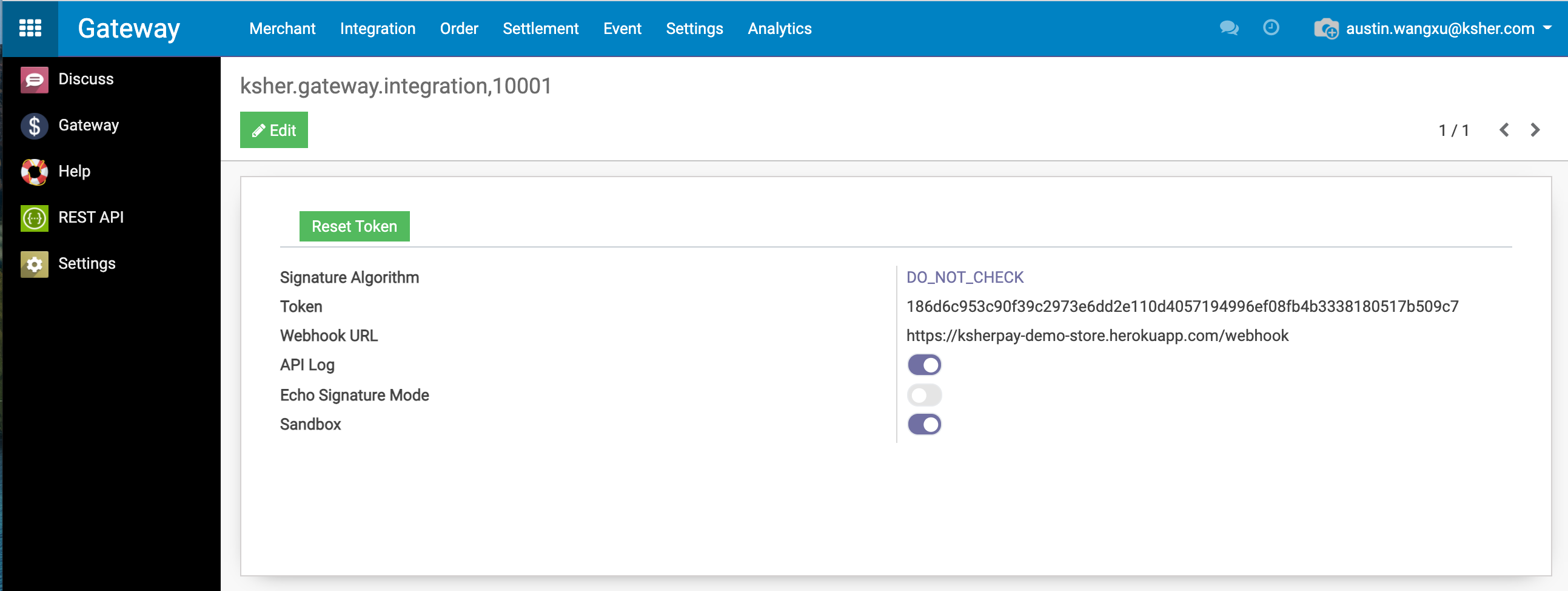
4.1. DO_NOT_CHECK#
You can disable the signature algorithm for testing purpose by setting it to "DO_NOT_CHECK"
4.2. Echo Signature Mode#
info
if Echo Signature Mode is on, all the API will be in echo mode, the reponse for each API call will be only with the valid signature and the input string of HMAC_SHA256 for debuging purpose.
Under the Integration -> Configuration menu of the gateway, you can open or close this signature calculation mode.
When the signature calculation mode is turned on, any request sent to the gateway will be used by the gateway to calculate the signature, and the calculated signature and the original string before the hash will be returned to the client to assist the client in verifying the implementation of the signature algorithm.
The following is an example of the return value after opening the signature calculation mode.
In the note field there is the original concatenated string before the HMAC-SHA256 operation, and there is the calculated hash value in the reference field.